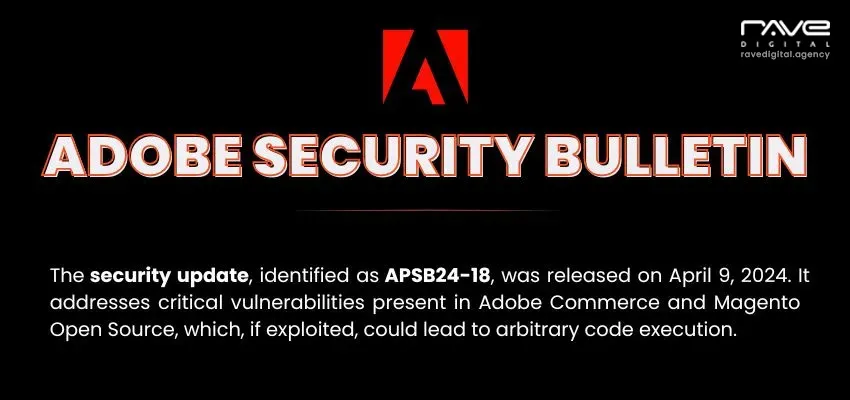
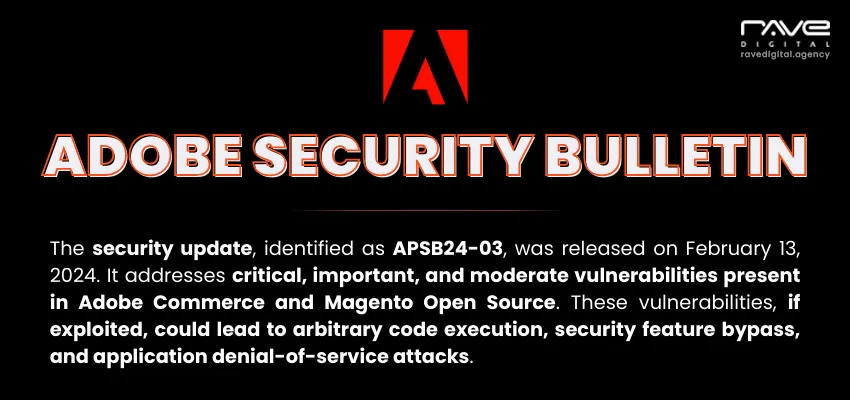
FBI has informed the public of a planted script via an outdated version of the MAGMI plugin, risking the vulnerability of credit card information and the likelihood of it being intercepted on any store running the outdated version of the plugin.
FBI has informed the public of a planted script via outdated MAGMI plugin, risking the vulnerability of credit card information and the likelihood of it being intercepted on any store running the outdated version of the plugin.
Magmi plugin – Magento Mass Importer developed as a Magento DATABASE client.
“
This type of attack is known as web skimming, e-skimming, or Magecart, and the FBI previously warned about a rise in attacks in October, last year.
Recent campaign exploiting MAGMI bug
In this recent campaign, attackers are exploiting CVE-2017-7391, a vulnerability in MAGMI (Magento Mass Import), a plugin for Magento-based online stores, the FBI said in a flash security alert sent to the US private sector at the start of the month.The vulnerability is a cross-site scripting (XSS) bug that allows the attacker to plant malicious code inside an online store’s HTML code.
The FBI says hackers are exploiting this vulnerability to steal environment credentials for a Magento online store, which they’re using to take full control over the targeted sites.
”
Source: zdnet.com
Recommended Steps to Avoid this kind of attacks:
- Update the MAGMI plugin to the latest version available, ASAP
- Update all plugins and extensions to the latest versions, ASAP
- Magento has announced EOL (End of Life) for Magento 1, i.e., June 30th, 2020, therefore, the Magento community is no longer focused on M1 plugins or extensions, yet another reason to migrate to M2!
What is Making My Magento Store Vulnerable?
Not maintaining your store or delay in M2 migration may put your store and your customers’ credit card data at risk. Magento Maintenance and migration is the need of an hour, especially for Magento 1 store owners and merchants. Magento has announced End of Life (EOL) for all the Magento 1 versions, i.e., no security patch or support updates after June 30th, 2020.