Adobe has recently released a critical security update for its Adobe Commerce and Magento Open Source platforms. The purpose of this blog post is to cover the specifics of this update, the possible risks it minimizes, and actionable steps users can take to strengthen their security posture.
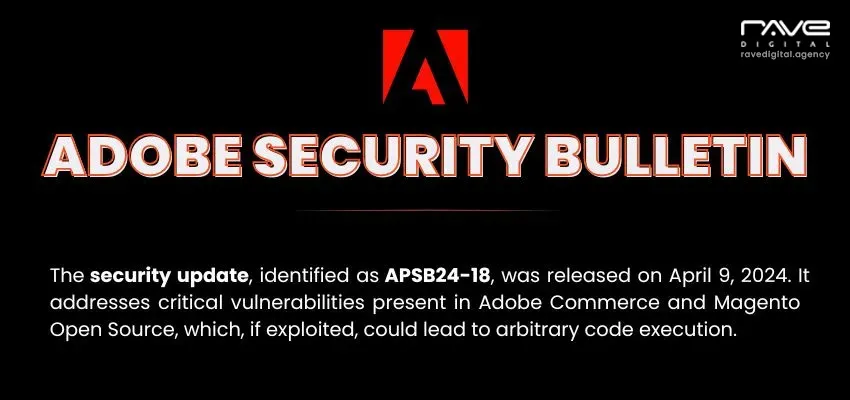
The security update, identified as APSB24-40, was released on June 11, 2024. It addresses critical vulnerabilities present in Adobe Commerce, Magento Open Source, and Adobe Commerce Webhooks Plugin. These vulnerabilities, if exploited, could lead to arbitrary code execution, security feature bypass, and privilege escalation.
Affected Versions
The affected versions include various iterations of Adobe Commerce, Magento Open Source, and Adobe Commerce Webhooks Plugin. Users of versions before the following are urged to take immediate action:
- Adobe Commerce: 2.4.7 and earlier, 2.4.6-p5 and earlier, 2.4.5-p7 and earlier, 2.4.4-p8 and earlier, and more.
- Magento Open Source: 2.4.7 and earlier, 2.4.6-p5 and earlier, 2.4.5-p7 and earlier, and 2.4.4-p8 and earlier.
- Adobe Commerce Webhooks Plugin: 1.2.0 to 1.4.0
Solution
Adobe has provided updated versions for both Adobe Commerce and Magento Open Source to address these vulnerabilities. Adobe has categorized the updates with the priority ratings and users are strongly advised to update their installations to the newest versions as soon as possible. Detailed installation instructions are available on Adobe’s website.
Vulnerability Details
The vulnerabilities encompass various categories, including Server-Side Request Forgery (SSRF) (CWE-918), Improper Restriction of XML External Entity Reference (‘XXE’) (CWE-611), Improper Authentication (CWE-287), Improper Authorization (CWE-285), Improper Input Validation (CWE-20), Unrestricted Upload of File with Dangerous Type (CWE-434), Cross-site Scripting (Stored XSS) (CWE-79), Improper Authentication (CWE-287) and Improper Access Control (CWE-284). These vulnerabilities pose the risk of arbitrary code execution, security feature bypass and privilege escalation.
You can find detailed information here: Adobe Security Bulletin APSB24-40.